Lessons from the MCP Breach: Shadow AI

About the Breach
In September 2025, security researchers at Koi disclosed a malicious backdoor in an npm package called postmark-mcp. Downloaded roughly 1,500 times per week, the package is used by developers in AI/automation pipelines to send transactional emails via Postmark.
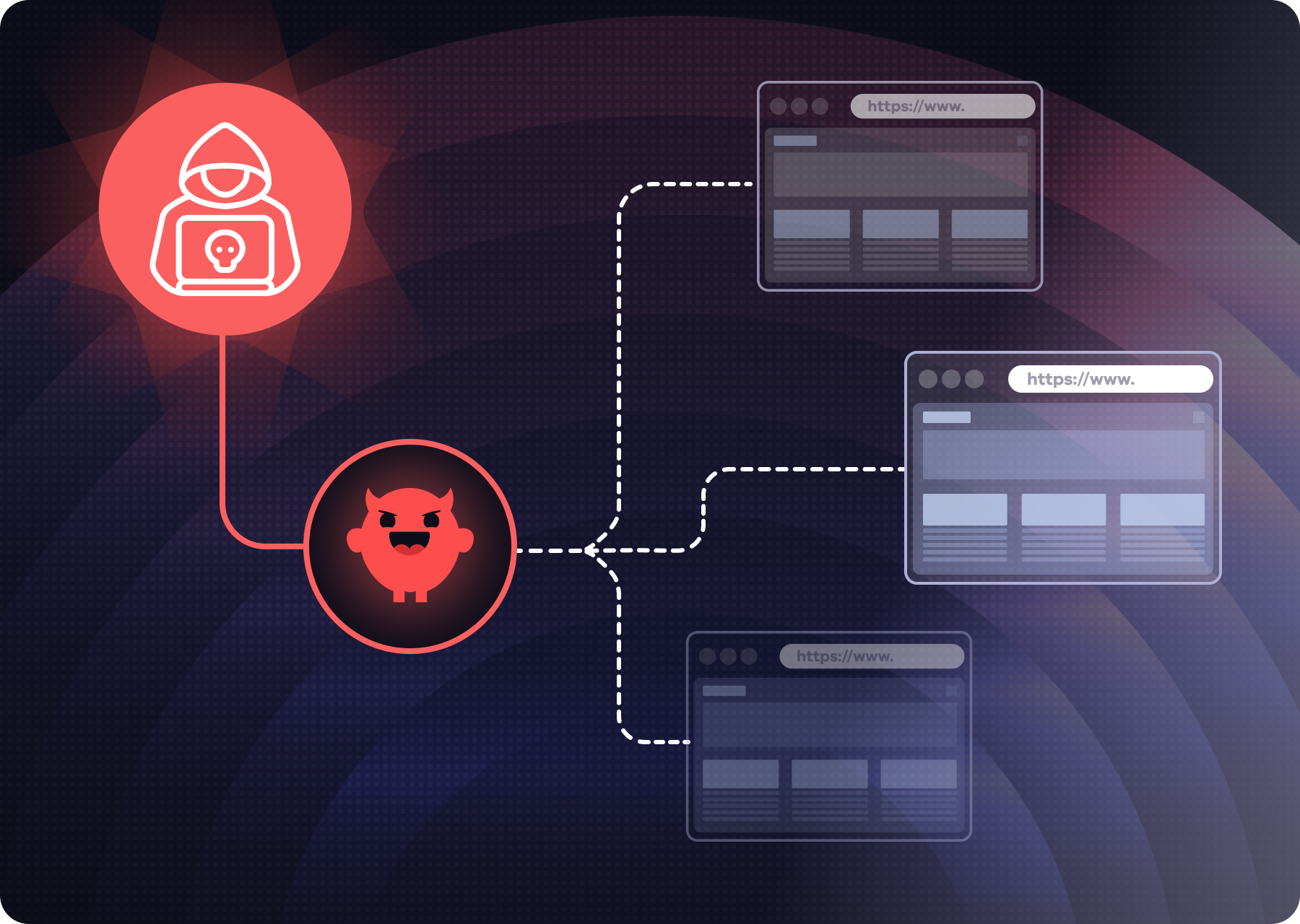
Everything seemed normal until version 1.0.16, when a one line of code was quietly added to BCC every outgoing email to phan@giftshop.club, effectively exfiltrating sensitive messages: invoices, password resets, and internal correspondence. The attack was stealthy: earlier versions worked as expected, earning trust, and the malicious version impersonated the official Postmark repo to evade suspicion.
Because MCP servers (Model Context Protocol) have deep privileges (they send/receive emails, may access databases, etc.), this breach was particularly dangerous. The attacker didn’t need a zero-day exploit or elaborate hacking: trust and automation did the work.
Why AI Endpoint Discovery Is Important
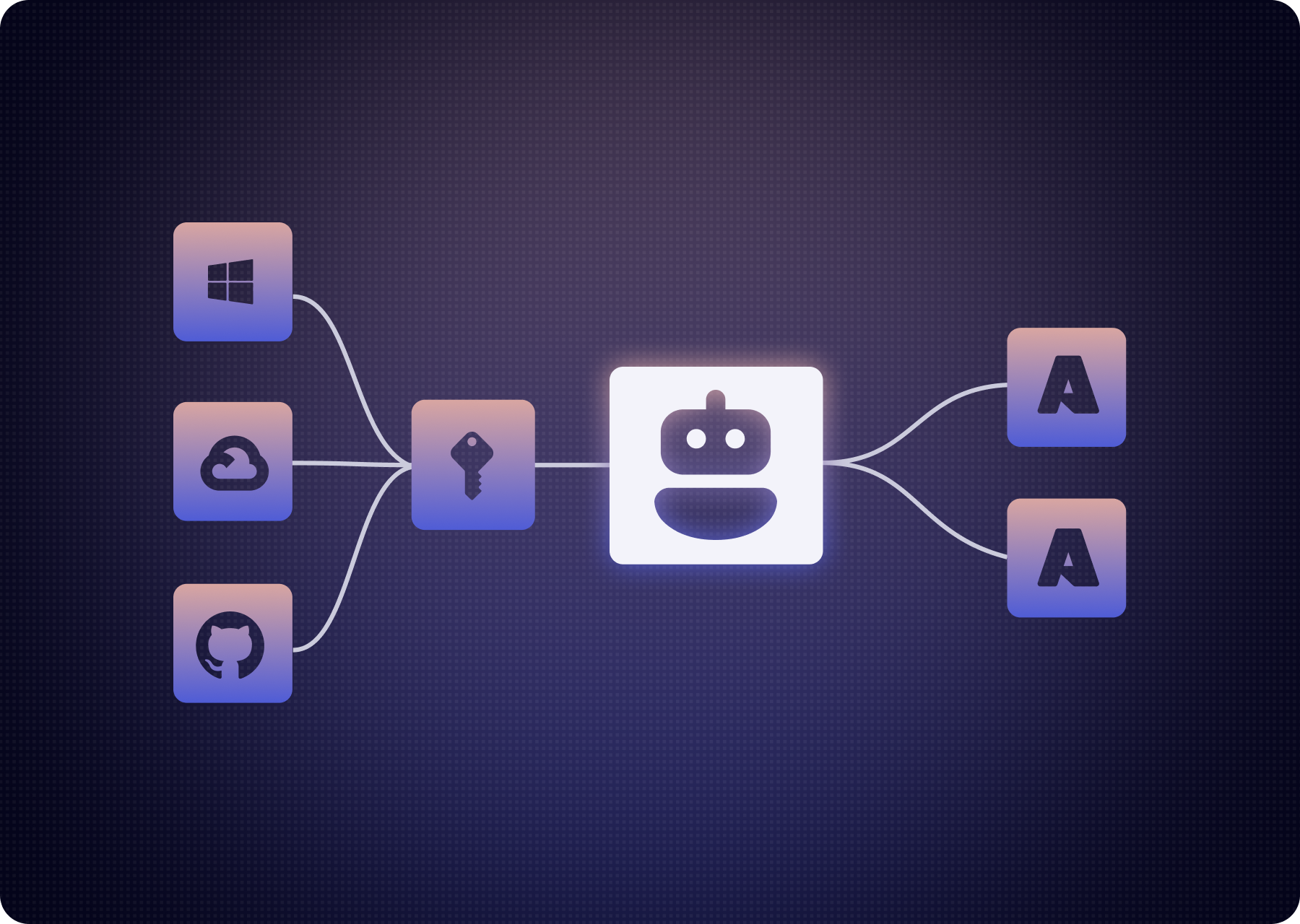
This incident underscores a deeper problem: where MCP tools often operate outside the traditional security perimeter and aren’t always tracked by asset inventories or vendor assessments. Once deployed, AI assistants or systems invoke them automatically, without human oversight, to carry out email workflows, database queries, or API calls.
If an MCP library or service is compromised, malicious behavior can persist unobserved for months. There’s little to alert standard security tooling (DLP, email gateways, endpoint protection) when the backdoor is embedded in a trusted tool.
By contrast, AI Endpoint Discovery means actively finding and cataloging all MCP and AI Agents in use across your environments (including “shadow” deployments). With full visibility, security teams can:
- Identify unapproved or high-risk MCPs
- Monitor AI Agent consumption of MCPs
- Enforce gating or approval policies before tools get deployed
- Quickly respond when a compromise is discovered
In effect, discovery is the first line of defense: you can’t protect what you don’t know you have.
How Oasis Helps
Automated Discovery & Inventory
Oasis continuously scans endpoints to identify all MCPs and AI Agents in use. This creates a live inventory of every automation tool across your environment, ensuring there are no hidden or “shadow” deployments operating outside of security visibility.
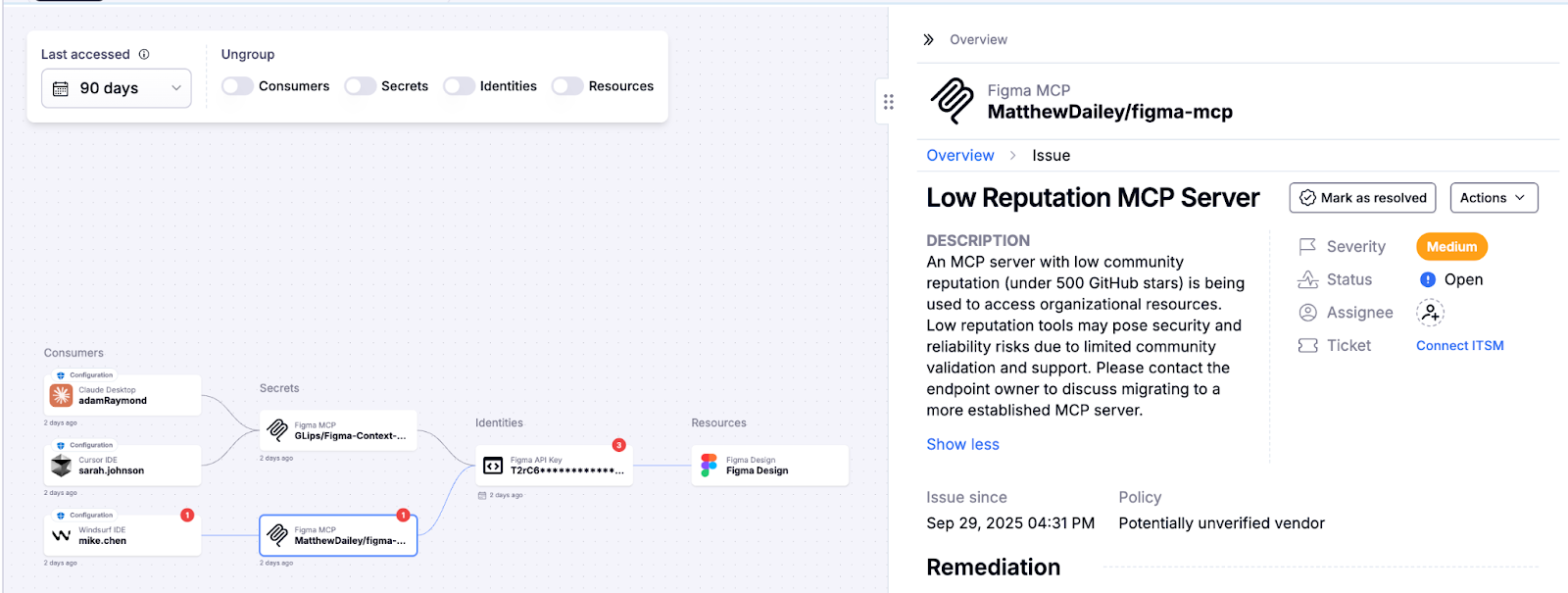
Identify Low Reputation MCP Servers
Oasis enriches discovered MCPs with reputation intelligence. If an MCP server or package is flagged as low-reputation or associated with malicious activity, Oasis notifies your security team immediately so it can be contained before damage spreads.
Remediation Guidance
When issues are detected, Oasis doesn’t stop at alerts. We help you gain clear context of the MCP or AI Agent owner, understand on which endpoints it runs and by whom, and provide actionable steps to resolve the issue. This ensures fast, confident remediation and reduces overall risk.
We do newsletters, too
Discover tips, technical guides and best practices in our biweekly newsletter.