How 2025 Changed the Way We Think About Identity Security

When Identity Met AI
For years, identity security followed a predictable model. Users logged in. Permissions were granted. Access was reviewed. That approach worked—as long as identities were human and actions were explicit.
In 2025, that assumption fully collapsed.
AI agents are now acting autonomously. Non-human identities (NHIs) multiplied across cloud and SaaS environments. Access decisions were no longer tied to logins or roles, but to digital workers making decisions, executing tasks, and interacting with systems at machine speed.
At the start of this year, one thing was clear: identity security had entered a new era.
When Identity Stopped Being Human
The shift didn’t happen overnight, but 2025 was the year it became impossible to ignore.
Security teams found themselves grappling with questions their tools weren’t built to answer.
- How do you govern access for AI agents that don’t “log in” or follow joiner-mover-leaver lifecycles?
- How do you understand intent when identities act independently?
- And, how do you maintain accountability when the fastest-growing identity population isn’t human at all?
Oasis entered 2025 focused on this problem.
From Managing Access to Governing Action
The rise of agentic AI forced a fundamental rethink. When software can reason and act, simply granting access isn’t enough. What matters is why access exists, what actions are allowed, how those actions are governed in real time. Crucially, this governance must be automated from the moment an identity is first created.
This thinking shaped what Oasis built in 2025.
We introduced Agentic Access Management (AAM™) — the first identity solution designed specifically to govern AI agents. Rather than extending human-centric models, AAM was built around intent-aware access, continuous policy enforcement, and clear accountability for agent actions.
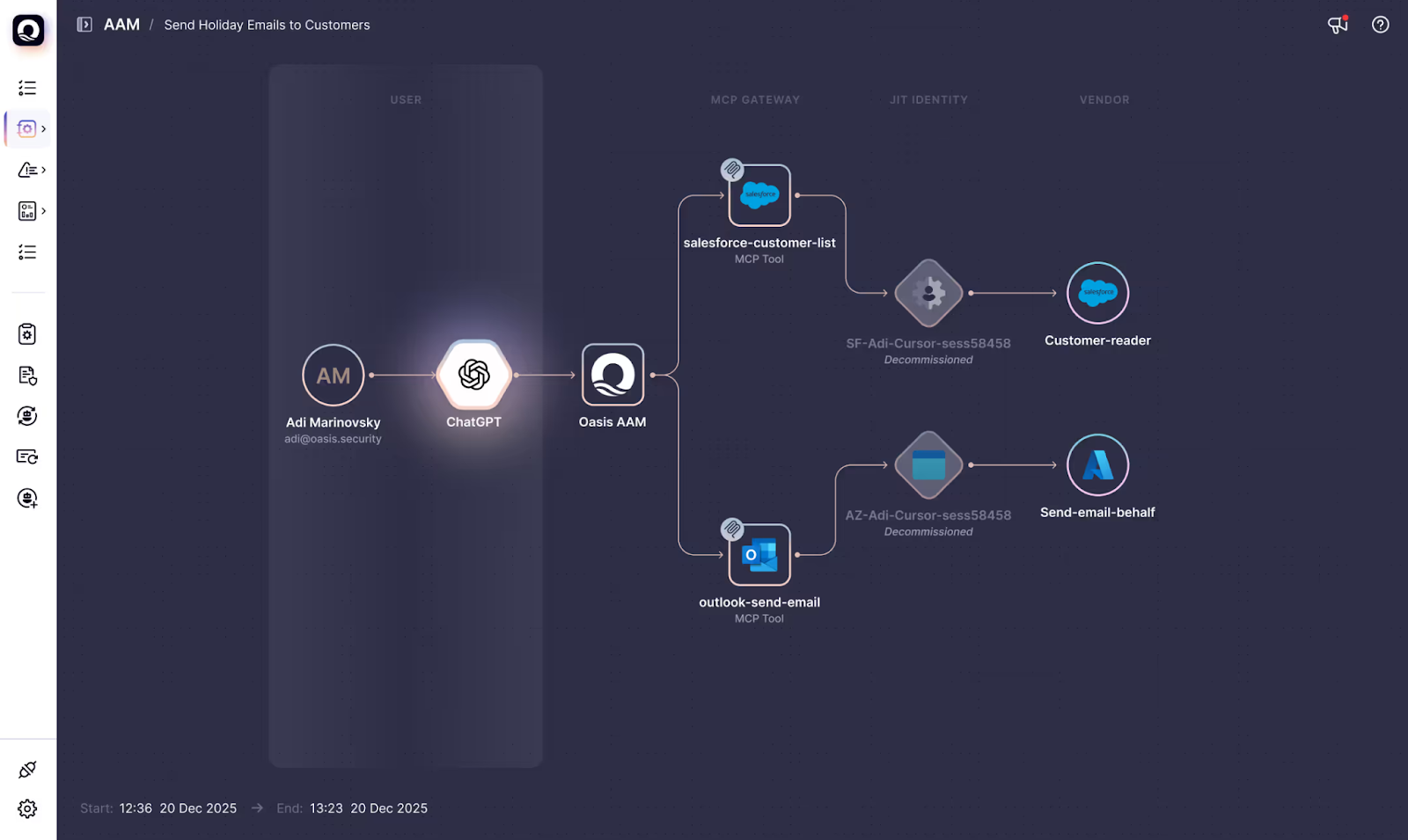
To help organizations operationalize this new category, Oasis also helped launch the Agentic Access Management Governance Framework, developed in partnership with industry leaders and practitioners. The framework gave security leaders a practical way to assess maturity and build governance for agentic AI access — pairing technology innovation with real-world guidance.
You can explore more about that work here:
As AI adoption surged in 2025, many organizations faced an all-or-nothing dilemma. The business wanted to move fast with AI. Security teams were being asked to approve systems they couldn’t fully govern. The result was a false choice: accept the risk, or hold the business back.
Agentic Access Management changes that equation — giving teams a way to say yes to AI innovation without sacrificing control.
Securing Non-Human Identities by Default
While agentic AI captured headlines, another shift was happening quietly in the background. NHIs— service accounts, API keys, and their associated secrets—became the largest and least-governed identity population in most environments.
In 2025, Oasis achieved several milestones to secure this lifecycle end to end.
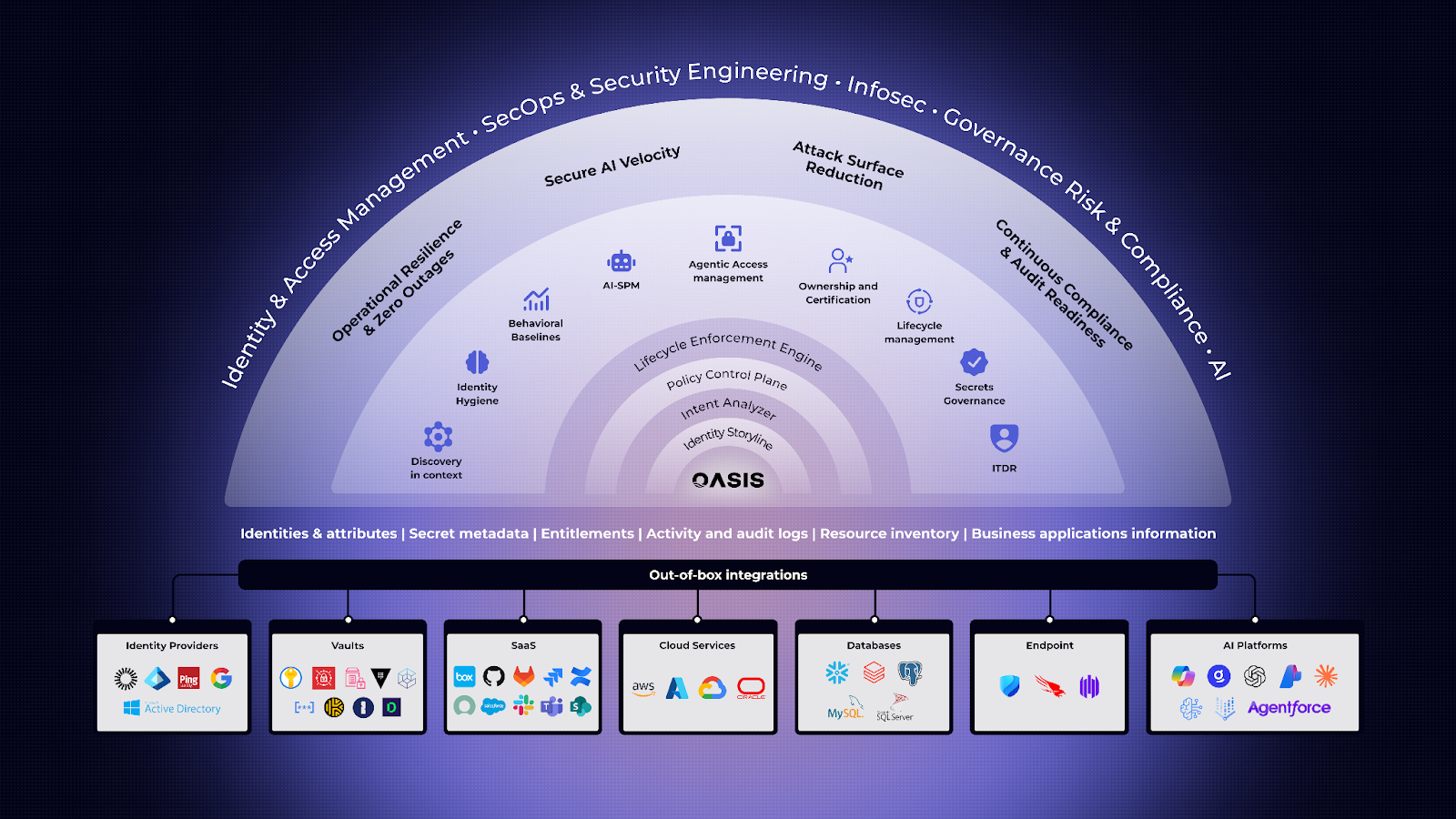
Oasis introduced NHI Provisioning to ensure non-human identities are created securely and governed from day one. To detect misuse, we launched Oasis Scout. In a world of screaming alerts, Scout acts as a filter—separating actual breach risks (the signal) from the background noise of daily operations. By understanding the intent and context of every identity, it ensures you only react to what matters.
To support the broader community, Oasis also released the Non-Human Identity Threat Center — the first public threat intelligence resource dedicated to attacks targeting non-human identities.
Together, these capabilities reflected a simple belief: non-human identities shouldn’t be an afterthought — they should be secured by default.
What 2025 Changed Forever
By the end of 2025, a few truths had become unavoidable.
Identity security is no longer just about authentication. It must understand intent. NHIs now outnumber human ones and often carry greater risk. And as AI systems become more autonomous, governing access without governing identity is no longer viable.
These lessons aren’t just reflections on the past year — they’re signals for what comes next.
Cheers to 2026!
As organizations head into 2026, identity is poised to become the control plane for AI. Access decisions will be evaluated continuously. Agent accountability will move from “nice to have” to mandatory. And security teams will shift from reactive controls to proactive governance.
The foundations laid in 2025 made that future possible.
At Oasis, the work continues. We are building identity security for a world where intelligence is distributed, autonomous, and deeply embedded in every system.
We do newsletters, too
Discover tips, technical guides and best practices in our biweekly newsletter.