The Agentic Access Management Framework: A Standard for Governing Agentic Access

Our Fortune 500 customers data shows AI-agent adoption up 840× YoY (from July 2024 to July 2025). Copilot agent creation grew 1,767%. At this pace, large enterprises will see agents outnumber employees by the end 2025.
Agents aren’t people, and they can’t be governed as if they were.
Assign ownership. Scope least privilege. Prefer federation over static secrets. Monitor actions. Retire fast.
Today we’re publishing the first practitioner-built framework, shaped with CISOs and visionary IAM leaders, to operationalize agent governance so AI speeds the business without widening the blast radius.
To make it actionable on day one, together with the theory we’re launching the AAM Self-Assessment: answer 10 questions, benchmark your posture in minutes, and get a prioritized action plan mapped to the AAM Framework.
Why a Framework Was Needed
AI adoption isn’t linear, it’s exponential, and it’s driven by identity and access.
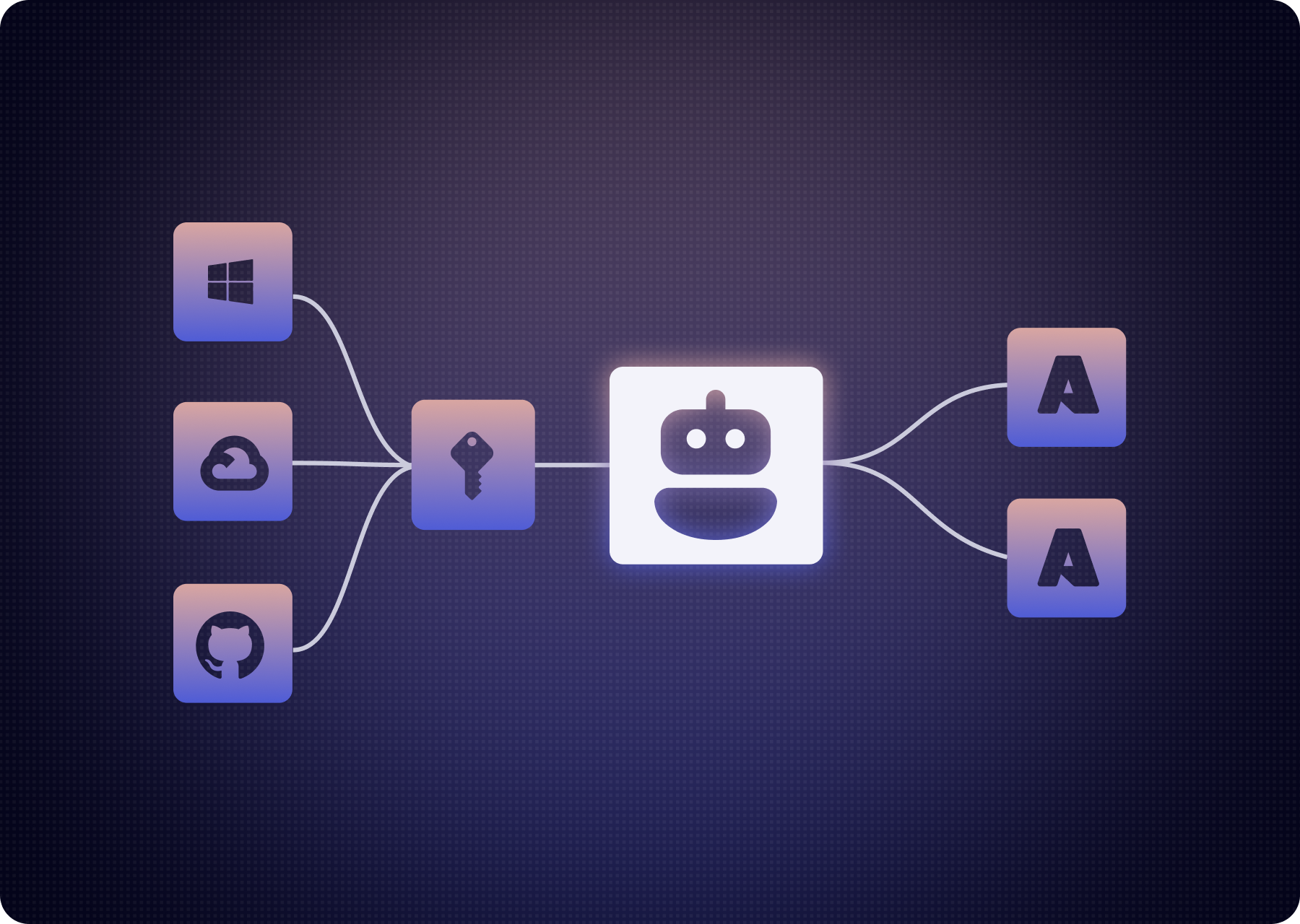
Every copilot, plugin, connector, or automation introduces non-human identities (NHIs) with access to corporate data and systems. What began as a few API keys or service accounts has exploded into thousands of active, autonomous NHIs with real privileges and minimal oversight.
Traditional IAM wasn’t built for this world. It assumes identities are static, human-controlled, and auditable. Agentic AI breaks every one of those assumptions. Agents run 24/7, and make access decisions on the fly. They spawn sessions, delegate tasks, and call APIs dynamically, often outside human approval loops. Each agent becomes a fresh access surface that can leak data, rack up cost, or be exploited.
When we analyzed agent-related incidents across large enterprises, five consistent themes emerged:
- Shadow AI: business units spinning up copilots or local agents without governance or IT oversight.
- Credential sprawl: hardcoded API keys and static tokens embedded in pipelines and notebooks.
- Excessive privilege: agents with broad access scopes far beyond operational need.
- Lack of ownership: no clear accountability for agent identities or their permissions.
- Monitoring blind spots: tools failing to distinguish legitimate AI behavior from threat activity.
These aren’t theoretical risks: they’re business-level exposures.
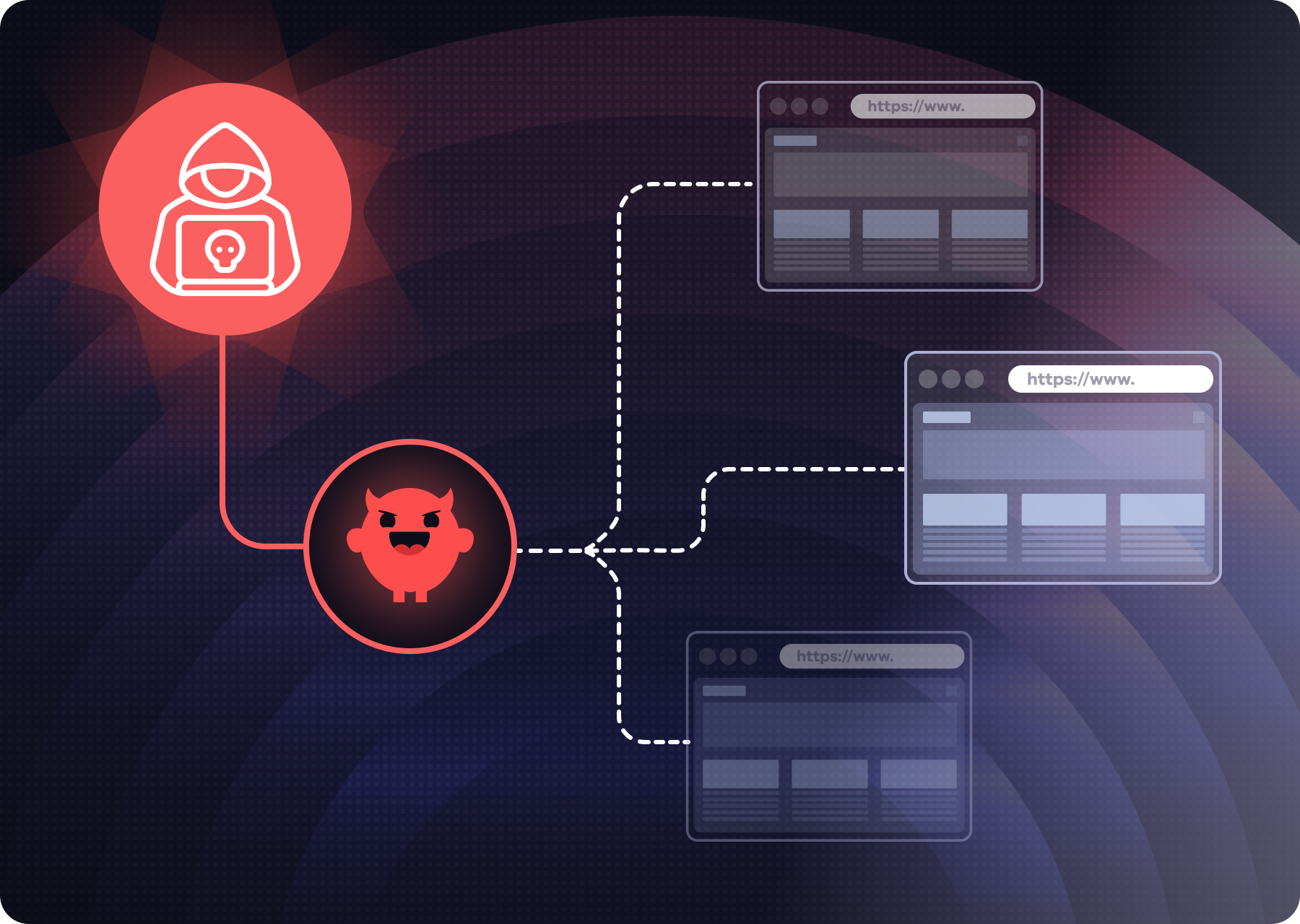
A single leaked model API key can cost tens of thousands per day in consumed tokens. A compromised connector can silently exfiltrate sensitive data to untrusted LLM endpoints. And as AI systems chain tasks across multiple environments, one compromised agent can trigger cascading privilege escalation. This isn’t hypothetical:
- Sysdig documented “LLMjacking” campaigns where stolen LLM API keys drove five-figure daily spend, with follow-on analyses noting victims racking up as much as $46k–$100k per day if undetected.
- On the supply side, Hugging Face Spaces disclosed stolen auth tokens, underscoring how compromised service credentials become high-leverage access paths for AI apps.
- In the enterprise, McDonald’s reported an AI-powered hiring system incident that exposed applicant data, proof that AI access paths can translate directly into large-scale privacy impact.
- And in the tooling layer, a recently disclosed Figma MCP integration flaw (CVE-2025-53967) allowed command injection and potential RCE against environments that connect agentic AI to design workflows, exactly the kind of agent-to-tool trust gap this framework is meant to close.
The problem isn’t AI itself, it’s unmanaged access. And that’s exactly what the Agentic Access Management Framework was built to solve.
Introducing the Agentic Access Management Framework
The Agentic Access Management Framework defines how to discover, govern, and secure every agentic identity, across models, tools, and data paths.
It’s built on seven pillars that turn AI access chaos into measurable control:
- Discovery & Inventory: Cataloging AI agents and NHIs and their relationships.
- Ownership & Accountability: Assigning clear human responsibility for each agent and identity.
- Credential Lifecycle & Hygiene: Secure provisioning, vault storage, rotation, and decommissioning.
- Access Security & Risk Management: Enforcing least privilege, quotas, and data loss prevention.
- Vendor & Service Trust Management: Classifying AI services, applying reputation scoring, and enforcing sovereignty requirements.
- Monitoring & Threat Detection: Detecting anomalous agent behavior and maintaining immutable audit logs.
- Risk Management & Continuous Improvement: Prioritizing controls based on risk, measuring maturity, and driving iterative improvements.
This framework isn’t theory. It’s a repeatable model any enterprise can operationalize using existing IAM, PAM, and cloud-native tooling. It aligns the speed of AI development with the rigor of access governance.
The AAM Check-in
CISOs asked for action over reading. We built a 5-minute calculator to turn reflection into a plan. Answer 10 questions across the seven pillars, using quick multiple choices and instantly receive your maturity stage and a prioritized governance roadmap.
Start the AAM Check-in to benchmark your program in minutes and get a prioritized action plan.
Closing Thought
AI is changing how work gets done, and who (or what) gets access. We don’t need to slow it down. We just need to govern it differently.
The Agentic Access Management Framework is that difference: a standard for governing access in the age of autonomous systems. Access the agentic access management framework here.
We do newsletters, too
Discover tips, technical guides and best practices in our biweekly newsletter.