How to discover, map, and secure AI Identities

In our previous blog post, we introduced the Agentic Access Management (AAM) concept, a shift from governing static non-human identities to governing agents that reason and act across systems.
This post focuses on the foundation of that shift: visibility.
Before you can control or govern agents, you must first discover them, understand what identities they use, what data they access, and who’s accountable for them. Visibility is the first step toward any form of AI governance.
From Models to Agents
A few short years ago, “AI” to most enterprises meant calling a model or two via API: pass some data, get a result. But today’s reality is far broader and deeper.
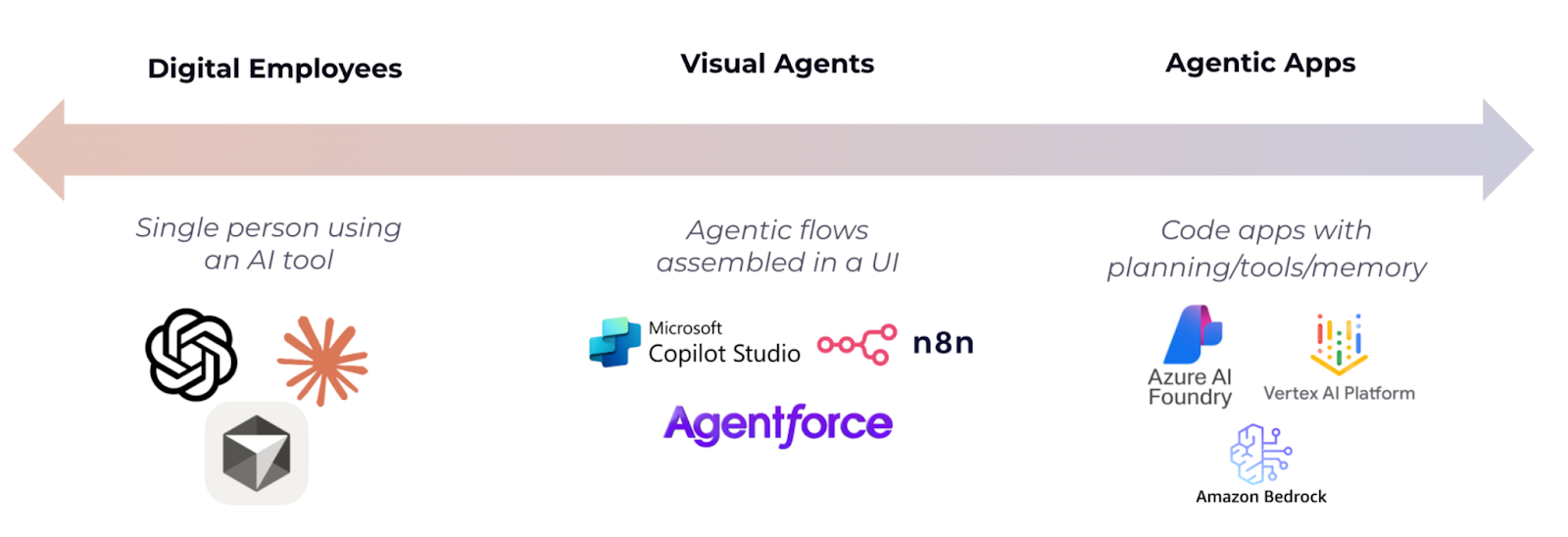
We now live in the era of AI services: platforms like Azure AI Foundry, AWS Bedrock, Google Vertex AI, and many others that host, orchestrate, fine-tune, and operate models at corporate scale. Alongside that shift, a new digital actor has emerged: AI agents.
AI agent landscape
Agents aren’t just LLMs. LLMs generate outputs when prompted; agents use LLMs plus connected tools and workflows to plan, act, and iterate toward goals (e.g., check a calendar, update a CRM, open a ticket). Interconnectivity is the value, and the risk. Agents are useful because they can reach into calendars, CRMs, SaaS apps, data lakes, and internal services.
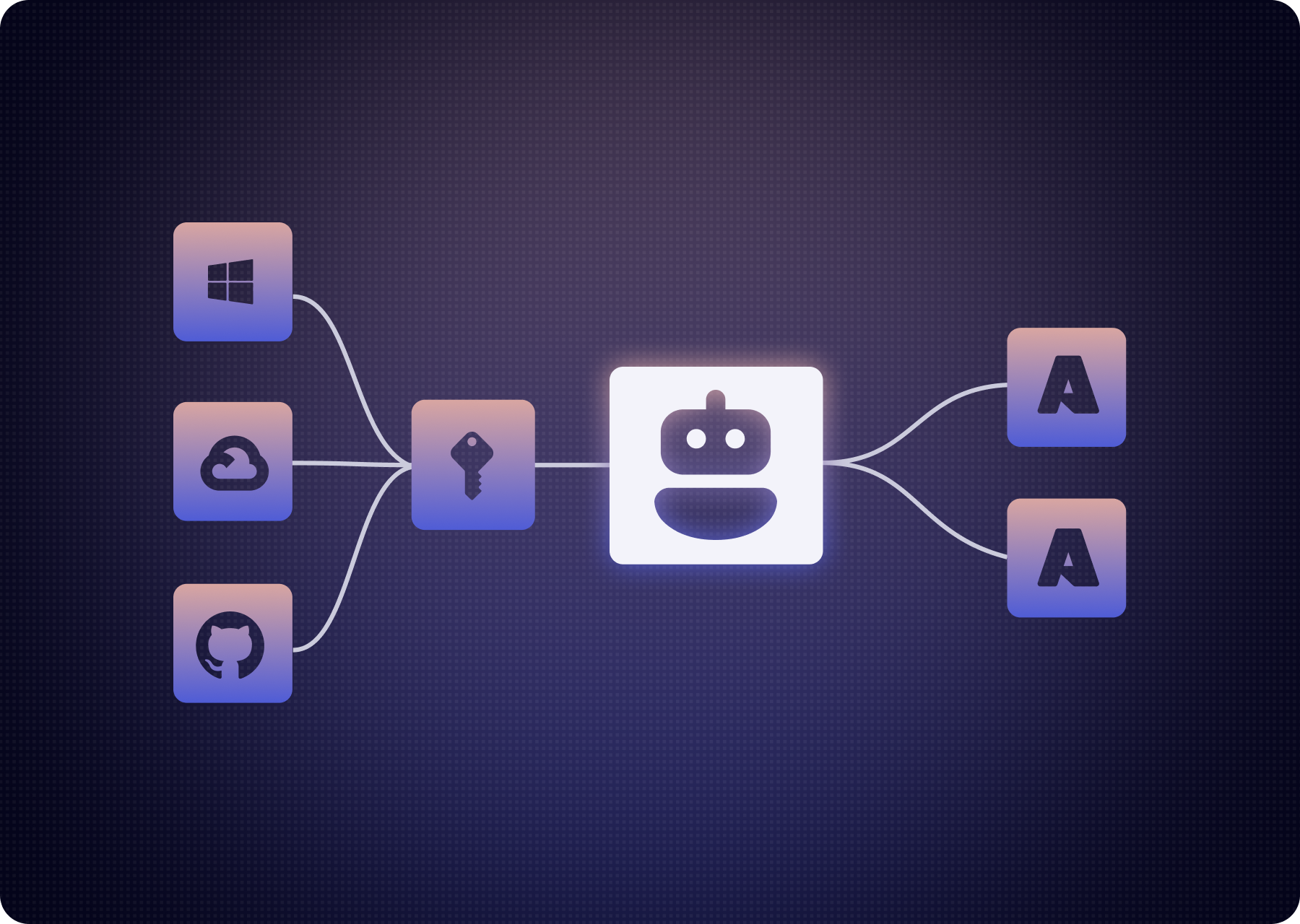
Every agent must carry identities to reach systems: API keys, OAuth tokens, service accounts, embedded SaaS permissions. In practice, each agent is an identity construct: permissions, secrets, behavior. Deploying an agent isn’t just shipping software; it’s introducing new identities with potential reach (and breach) across your estate.
While we’ve spent years refining how we manage human and non human identities (users, privileged admins, service accounts), the world of model-driven, agent-based identities is not standardized, loosely governed, and aggregating risk via:
- Proliferation: thousands of agents, many with secrets and keys, accessing systems.
- Lack of Visibility: how many agents do we have? Which identities are they using? Which agent is doing what? When? What data does it access?
- Ambiguous ownership: who “owns” the agent and its identity lifecycle? Loose change management means orphaned or forgotten identities.
- Lack of accountability: Employees hold accountability for their actions, and engineering and operational teams are accountable for software they test and deploy. But who’s accountable for what an agent does?
Put simply: The new era of AI isn’t simply about new models or new business opportunities; it’s about new identity surfaces.
As one IAM principal from a Fortune 500 company put it: “We’re seeing dozens of ‘assistants’ created in our systems. They each have keys. But we don’t even know who owns many of them, much less what they’re allowed to do.”
The Governance Gap
Most enterprises are still in an “adopt first, secure later” mindset. That leads to a predictable cleanup cycle: hundreds of agents, scattered tokens, and overlapping privileges.
Without visibility, you can’t prioritize or remediate risk.
Some of the most common challenges we see include:
- Discovery: Agents appear across SaaS, cloud environments, and endpoints, often inheriting user tokens without registration or metadata linking model, tools, credentials, and owner.
- Secret sprawl: Static keys buried in configs and scripts, with unclear dependencies when rotated.
- Context gaps: Which model powers which agent? Is it approved? Governed?
- Over-permissive access: Agents quietly acting with broad privileges and touching sensitive data.
- Compliance pressure: Regulations like the EU AI Act and NIST AI RMF demand traceability and auditability, which is impossible without managing agents and the NHIs they leverage.
The Oasis Approach: Securing AI through Identity
At Oasis, we see AI agents as a new class of digital actors that use identities to reason, decide, and act.
Each agent operates through a web of non-human identities (API keys, service accounts, OAuth tokens) that grant it reach across systems. This creates a new scale of access, and a new kind of governance challenge.
To manage this responsibly, agents must have their own lifecycle: from creation and permissions mapping, through ownership attribution and credential management, to secure decommissioning.
By applying identity discipline to these new actors, discovering the NHIs they rely on, mapping their access and relationships, and governing their lifecycle, organizations gain the visibility and control required for secure AI adoption at scale.
In short, Oasis brings order to the growing web of autonomous access, transforming agentic AI from a governance blind spot into a governed, auditable layer of enterprise infrastructure.
Discovery & Context
We discover and map every AI service and agent, whether SaaS-based or locally deployed, along with the non-human identities they leverage, the secrets they use, the permissions they hold, and the behaviors they exhibit.
This process answers critical questions: What agents exist in my environment? What credentials do they rely on? What systems and data do they access?
It provides unified visibility across the entire AI estate, far beyond human users or static service accounts.
AI platforms we support

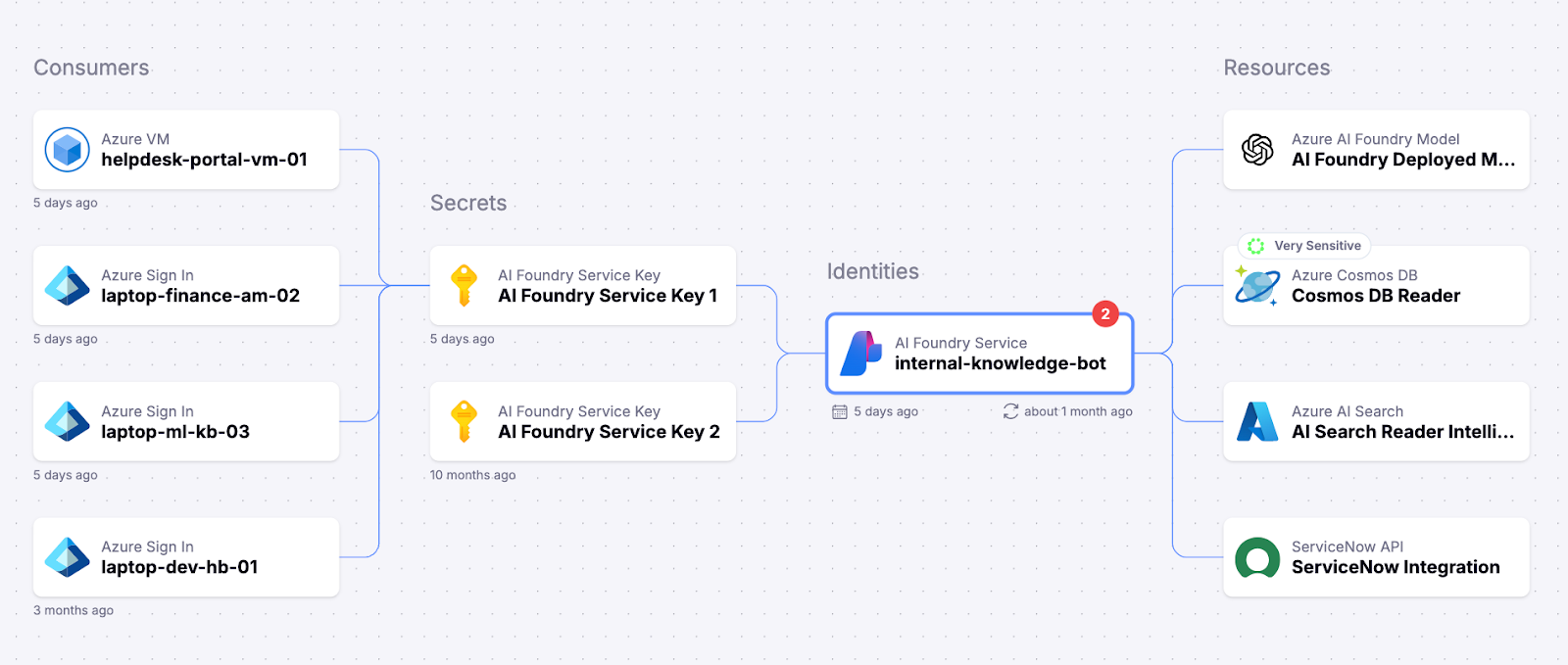
Unfederated, Overprivileged Azure Foundry agent:
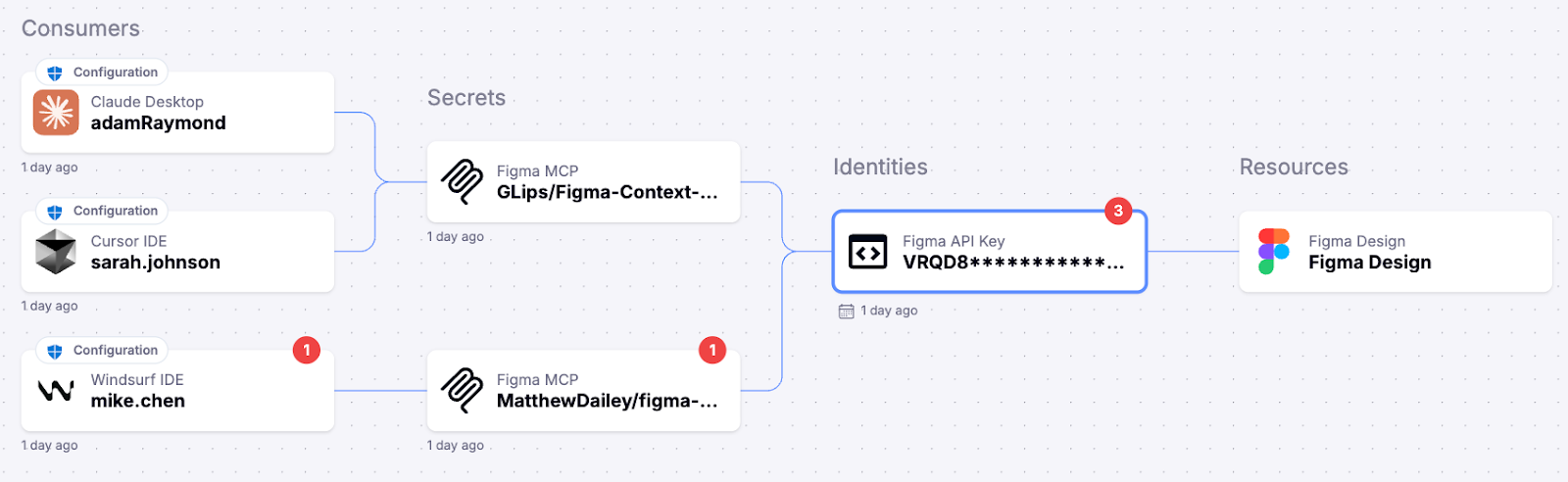
Overused Figma API key leveraged by locally deployed AI agents:
Identity Posture & Risk Scoring
Once AI assets are discovered, understanding their posture becomes essential.
At Oasis, we evaluate every agent and NHI, map and manage their lifecycle. Our platform analyzes how each agent interacts with data and systems, which assets it touches, how frequently it operates, and whether it aligns with organizational policies and best practices.
This produces a dynamic risk score that reflects real-world context:
- Is it privileged?
- Is it accessing high-sensitivity data sources?
- Has its owner left the organization, or has it gone dormant?
- Is its activity pattern consistent with legitimate use, or drifting into anomalies?
High-risk or anomalous activities surface automatically, allowing security teams to investigate and take action before misuse becomes breach.
Ownership as the Anchor of Accountability
Ownership is the anchor of accountability in the AI era. As agents proliferate across teams and business units, each spun up to automate a task, integrate a tool, or assist a workflow.
The question of “who owns this?” becomes more than an administrative question. It defines who is responsible for the lifecycle, permissions, and risk surface. Without explicit ownership, agents drift, persisting long after their creator moves on, carrying active credentials and system access. In large organizations, this turns into a silent sprawl of orphaned identities.
AI Compliance Offering
We have built a comprehensive agentic AI access-management solution grounded in a seven-pillar framework:
- discovery and inventory
- ownership and accountability
- credential lifecycle and hygiene
- access security
- vendor trust
- monitoring and threat detection
- continuous risk improvement.
Our platform delivers full visibility into AI systems across local and cloud environments, mapping both inbound and outbound access. It automates ownership recommendations, enforces credential lifecycle controls, assesses vendor risk, and continuously monitors for threats and policy violations, ensuring secure, governed, and trustworthy AI deployment at scale.
Key takeaway
Every agent you deploy, whether a copilot, workflow, or custom model, becomes a new actor in your infrastructure.
Securing AI isn’t about locking down models; it’s about governing the identities behind them.
When visibility comes first, governance follows naturally, and the foundation for secure, scalable AI is set.
Oasis Security helps enterprises build that foundation: discovering every agent, mapping every identity, and enabling safe, accountable AI adoption.
Want to see how this works across your tenant in minutes? Get a live demo of Oasis, we will run through your use cases, surface quick wins, and leave you with an action plan.
We do newsletters, too
Discover tips, technical guides and best practices in our biweekly newsletter.