What is Agentic Access Management?
For two decades, identity programs were built around humans. We mastered SSO, MFA, approvals, reviews, PAM; tying every action to a person, a role, an audit trail. Those controls scaled because access mapped cleanly to employees and their jobs.
Then non-human identities (NHIs) exploded: service accounts, API keys, cloud roles, bots. Security teams learned to treat NHIs like first-class identities: discover them, assign ownership, rotate secrets, deprovision at end-of-life. Non-human Identity Management (NHIM) brought order to a sprawling machine layer and showed measurable maturity steps from ad-hoc hygiene to automated lifecycle and risk-driven controls.
But something new is happening. A new type of actor has entered the ecosystem, one that doesn’t just connect systems, but decides how to use them.
The new layer above NHIs: agentic access
AI agents don’t just connect systems; they reason, decide, and act.
Enterprises are creating them fast; in some environments agent growth has already outpaced headcount.
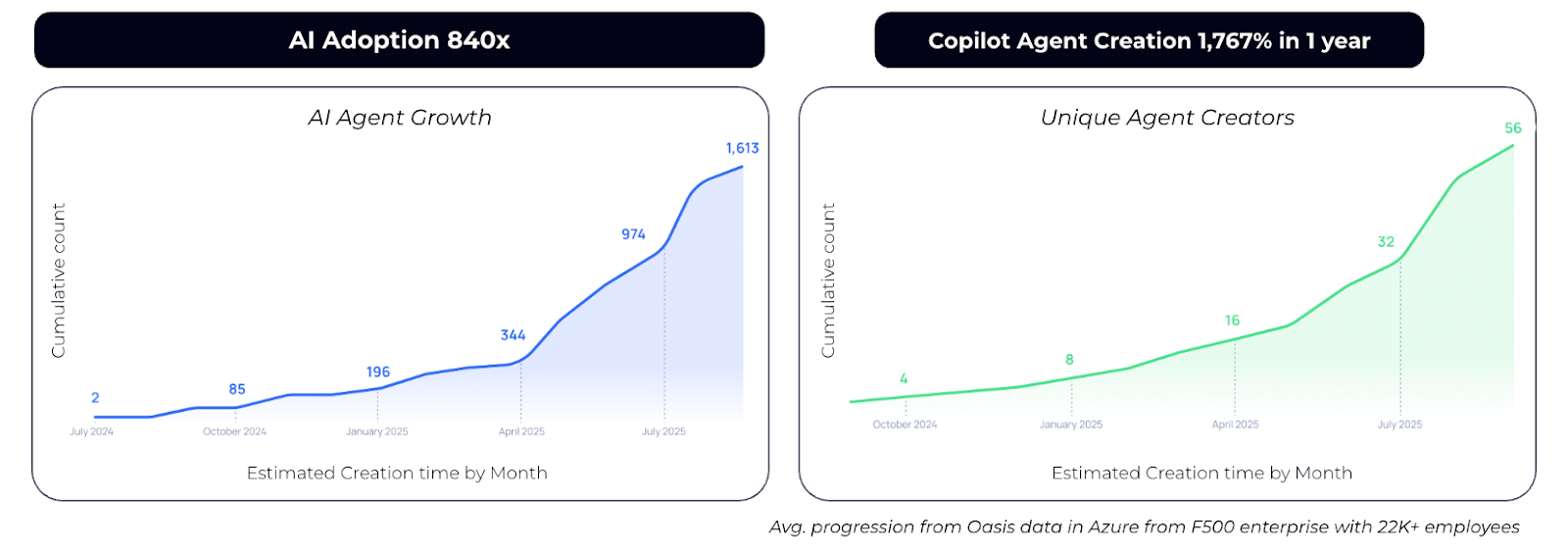
Why NHIM alone can’t solve this
NHIM governs deterministic actors. Agents are dynamic: they interpret intent, request access on the fly, and chain tools in ways IAM/PAM never modeled. That breaks accountability and observability: who asked for what, why, and under which guardrail?
It’s the “synthetic middle” between human and app access: prompt-driven like a user, automated like software.
This isn’t a mere technicality. It’s a critical distinction we have to confront. We train, monitor, and hold our employees accountable for their actions. We trust their reasoning and judgment. When developing applications, we follow a disciplined Software Development Lifecycle (SDLC) to ensure our systems behave predictably across a wide range of inputs. We trust the process, and reinforce it with strong identity guardrails.
By contrast, the agentic access pattern neither earns our trust nor benefits from the same SDLC rigor that governs traditional applications. It allows a single flawed judgment call to be executed at scale and in production.
So… why Agentic Access (coming from NHIM)?
In physics and engineering, you tame new complexity by reducing it to a form you already know how to solve. That’s our approach to agentic access.
AAM is the translation layer that converts agent intent into the IAM controls we already trust: Identify → Intent → Control Choice → Audit
- Who is the actor behind this access request? And what agent is he using?
- What does the agent intend to do?
- Then: issue a JIT ephemeral session (seconds/minutes)
- Always: record the full trail (person, agent, prompt, policy, actions, teardown).
The session is the measurable unit of the AI era. Instead of years-long accounts, we govern seconds-to-minutes sessions: each one a bounded, explainable transaction. Same questions as always: who, what, why, just answered at session speed.
When supporting a repeatable session, we can extend this time-bound behavior to enable automations; managing a persistent, secretless, or periodically rotated NHI while still preserving a per-session audit trail.
What is Agentic Access Management (AAM)?
Agentic Access Management (AAM) is the practice of discovering, securing, and automating the lifecycle of agents and the non-human identities they utilize. Practically, it adds three capabilities on top of NHIM:
- Intent inference: Understand what the agent is trying to do: who invoked it, for what data, toward which goal, so policies evaluate purpose, not just API verbs
- Deterministic policy enforcement: Validate the requested action against codified guardrails (not just prompts). Approve inline, escalate with human-in-the-loop at privilege boundaries
- Just-in-time (JIT) session identities: Provision ephemeral, scoped identities per session; no standing secrets, secure connection brokering without credential exposure, automatic teardown at end of task, full session trace (person, prompt, policy, actions).
The Oasis approach - Stay tuned!
- Discovery & visibility across agent types and their credentials/permissions, even when granted via MCP-style gateways.
- Intent-aware policy with deterministic enforcement and inline approvals.
- JIT identities for agents: ephemeral, least-privilege sessions with full traceability and automatic teardown.
The result: agents stay fast; access stays accountable.
Want the playbook? Explore the Agentic Access Management framework for best practices.
What’s next
In our next blog, we’ll go deeper on the three landscape categories, how they show up in Azure AI Foundry, Bedrock, Vertex AI and SaaS ecosystems, and the operational patterns to watch.
We’re also preparing an exciting product announcement that brings these ideas to life, stay tuned for details soon.
If you’d like to see how this looks in your environment: discovery, ownership, posture, and JIT sessions, reach out and we’ll walk through a live tenant review.
We do newsletters, too
Discover tips, technical guides and best practices in our biweekly newsletter.