Introducing Oasis Agentic Access Management

Today, we’re introducing Oasis Agentic Access Management (AAM™).
It’s an industry-first, although it's been a long time in the making: Oasis AAM™ gives enterprises clear, accountable control over what AI agents can do in their environment. It removes the uncertainty around agent access by turning every action, whether reviewing pull requests, modifying production records, or triggering workflows in critical systems, into a controlled, time-bound, least-privilege session with only the exact permissions required, and nothing more.
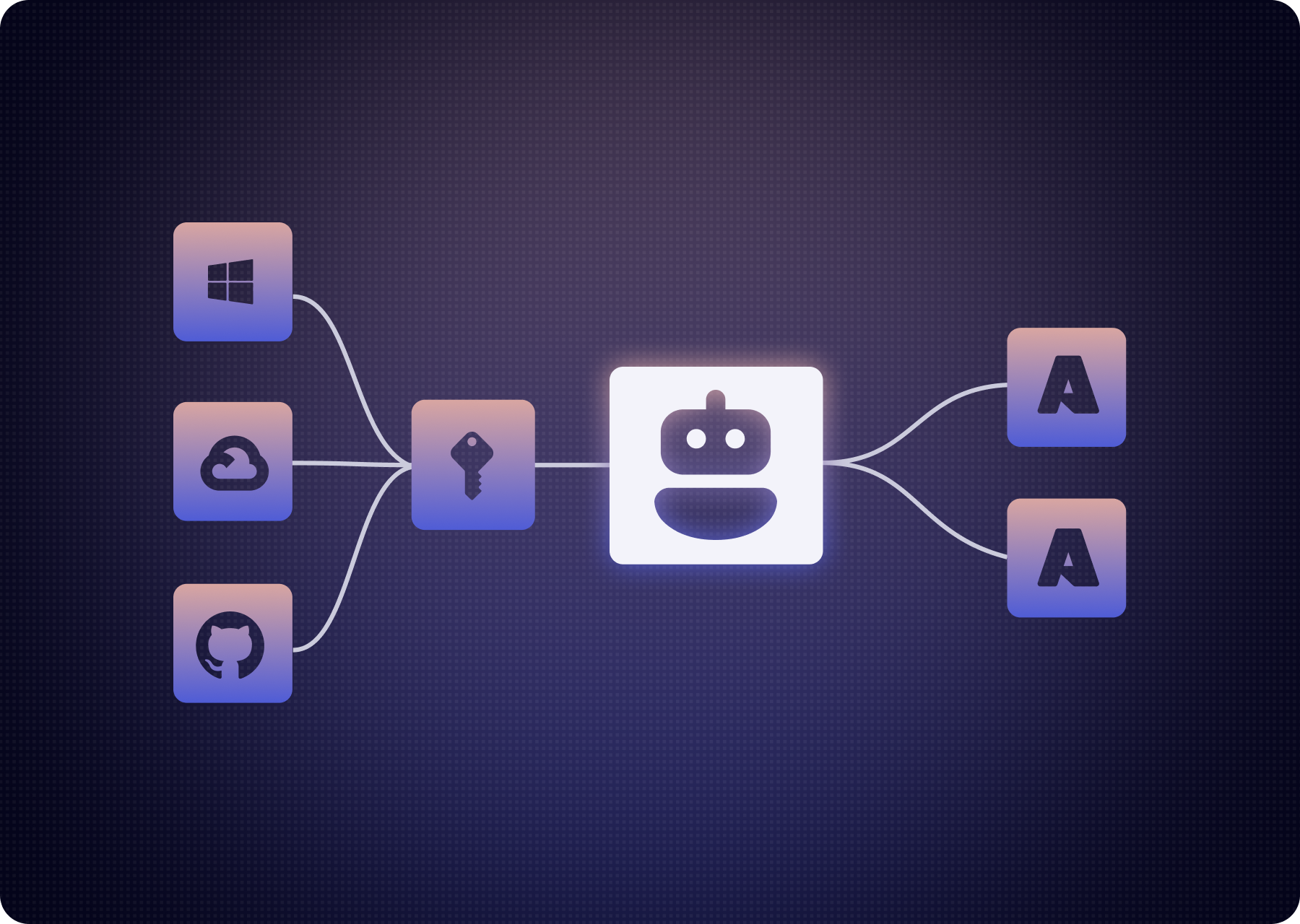
From day one, Oasis has empowered identity teams to get control over non-human identities (NHIs): service accounts, service principals, applications and roles across on-prem, cloud, and SaaS. With AI agents now acting on top of those same systems, AAM extends that foundation to govern the agents themselves and the access paths they depend on.
With AAM, organizations can streamline agentic access by defining unified policies that let security teams safely enable the business over ever-evolving infrastructure. AAM helps organizations:
- Protect enterprise data, by controlling and securing the permissions AI agents can use for each request.
- Reduce AI-driven risk, by eliminating standing privileges and enforcing short-lived, least-privilege access for every agent action.
- Improve governance and auditability, by tracing each AI request from intent to action with a complete, prompt-level audit trail.
Why Now
Oasis first set out on a mission to help enterprises everywhere deal with identity access, specifically NHI ones. So it was a natural next step for us to build a solution for enterprises to deal with the fastest-growing challenge (and opportunity!): agentic access. AI agents have reached the enterprise faster than anyone expected. What started as simple copilots summarizing tickets or drafting emails has become agents operating directly on production systems, CRMs, data warehouses, ticketing systems, code repos, and internal services.
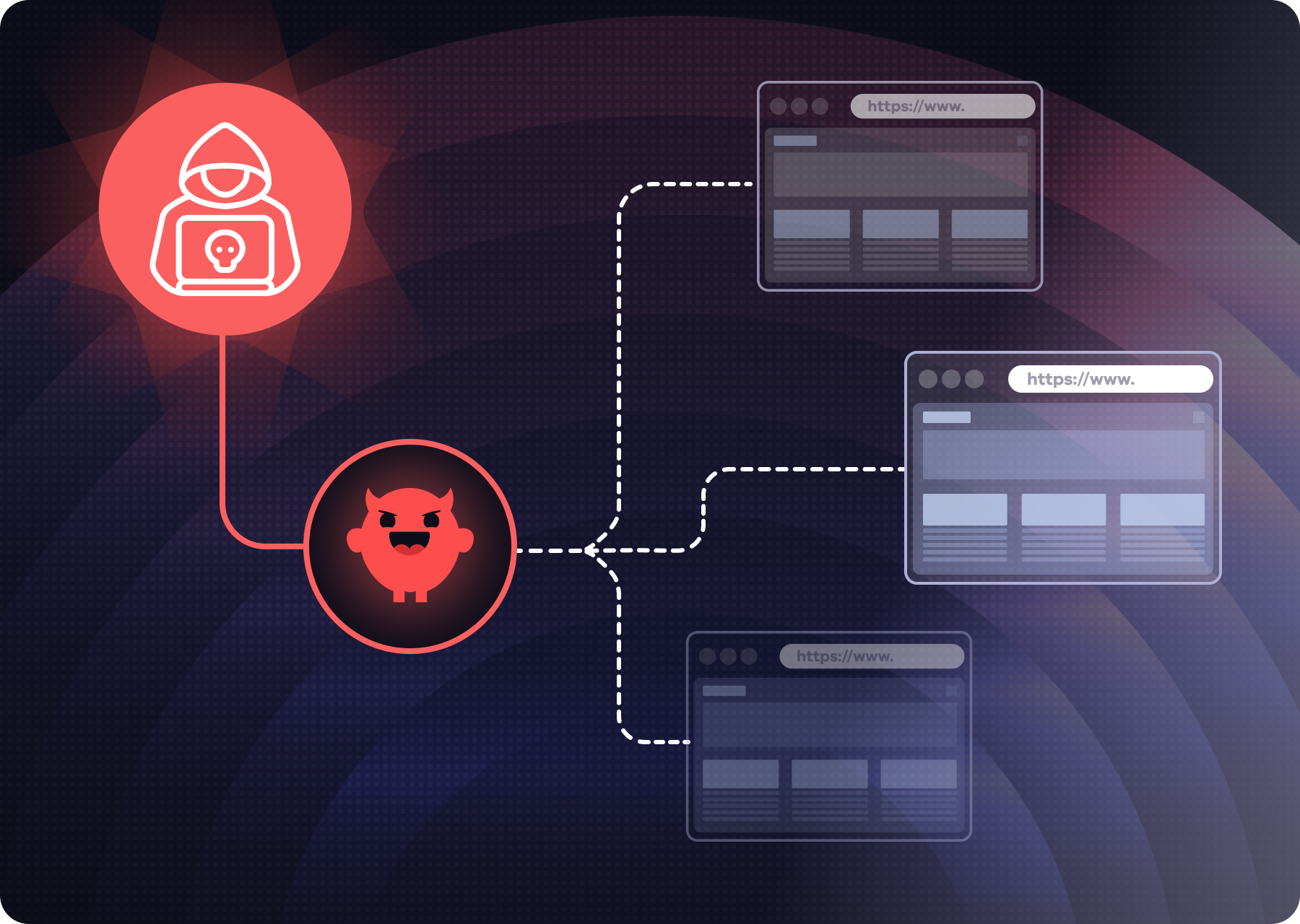
The challenge was clear to us: AI agents already have access. Enterprises just don’t have a way to control it.
Teams connect agents through delegated access with OAuth tokens or by reusing human access. Agents inherit broad permissions, identity teams can’t see or govern the resulting access paths, and when something goes wrong, it’s nearly impossible to explain who approved what, or why the agent acted the way it did.
Most organizations struggle to answer, with confidence:
- Which agents are connected to which systems and data?
- What permissions those agents currently have?
- Who approved the access, and for what purpose?
- What actions did the agent take, and why?
- How to limit an agent to just the task it was asked to perform?
This leaves them stuck between two bad options:
- Adopt first, secure later, hoping nothing breaks.
- Block by default, slowing down AI initiatives.
Neither scales. A new access model is required.
What is Oasis AAM?
Oasis AAM™ is an intent-aware, policy-driven identity infrastructure that governs how AI agents access enterprise resources.
It sits between your agents (copilots, assistants, automations) and the systems they touch (SaaS, cloud, on-prem, data platforms). Every interaction is turned into a short-lived, least-privilege session with full accountability.
Instead of handing agents static credentials or broad OAuth grants, AAM ensures that access is:
- Requested with clear intent
- Evaluated deterministically against enterprise policy
- Granted via just-in-time, ephemeral identities
- Tracked with full end-to-end accountability
Access is not granted once and forgotten; it’s evaluated in real time, per action and per purpose.
How Oasis AAM works
Oasis AAM turns agent requests (prompts, tool calls, or action plans) into governed sessions through four core capabilities:
- Intent understanding
AAM analyzes each agent request (prompt, tool call, or action plan) and turns it into structured intent: which resource, which operation, which scope, and for what purpose.
A natural-language prompt becomes a clear, auditable intent.
- Deterministic policy enforcement
Every intent is evaluated against enterprise guardrails, for example:
- Block destructive actions in Databricks
- Allow read-only access to production databases
- Require escalation for write operations in CRMs
- Restrict configuration changes to approved environments
Policies, not prompts, drive the final decision. This creates predictable, auditable behavior across all agents and systems.
- Just-in-time, ephemeral identities
If a request is permitted, AAM provisions a short-lived identity scoped only to the required action. These identities:
- Have no standing privileges
- Contain no long-lived secrets
- Are automatically decommissioned when the task ends
In practice, AAM issues the minimum permissions required for the specific intent, uses them for the session, then tears them down. Long-lived access paths are removed from the equation.
- Full context and auditability
Every session generates a complete chain of custody: Human → Agent → Prompt → Intent → Policy → Identity → Actions → Results
Identity, security, and compliance teams gain the visibility and accountability they have been missing, supported by regulator-ready evidence for AI governance.
See it in action
A marketing copilot receives the prompt:
“Follow up with all leads from our Q3 marketing campaign. Draft personalized emails for each lead.”
To complete this task, the agent must:
- Read leads from Salesforce
- Send emails via SendGrid
Without AAM:
- The agent uses broad OAuth token for Salesforce and SendGrid
- It can read or update any CRM or email records those identities touch
- It can send emails to any recipient
- There’s no clear record of who approved the access or what the agent actually did
- A single mistake (or hallucinated action) has a massive blast radius
With Oasis AAM:
- The prompt is converted into structured intent:
- salesforce_get_leads (Q3 campaign leads only)
- sendgrid_send_email (only to those leads)
- Policies evaluate whether this workflow is allowed for Liam Rodriguez’s agent
- A short-lived identity is issued with only:
- Salesforce: leads.read for the relevant campaign
- SendGrid: emails.send for approved recipients
- The session is monitored and destroyed after use
- A visual audit trail shows the full path:
Liam Rodriguez → ChatGPT → Oasis AAM → Salesforce (leads.read) → SendGrid (emails.send)
Business teams move fast. Identity and Security teams stay in control.
Why AAM Matters
- Contain agent blast radius: Stop agents from holding broad, long-lived grants that nobody remembers to revoke.
- Achieve real AI governance: Prove to auditors and regulators exactly how agents access data and systems, backed by end-to-end chain-of-custody.
- Unify access for NHIs and agents: Use a single platform to govern the full spectrum of identities powering your automations and agentic applications.
- Say “yes” to the business, safely: Teams can adopt agents freely, backed by strong identity-layer guardrails.
Completing the agentic access spectrum
Oasis already governs the NHIs powering your automations and agentic applications. With AAM, we now govern the agents acting on top of them, completing the full agentic access spectrum: from underlying service identities through to the AI agents your employees use every day.
See Oasis AAM in action
If you’re asking: “How do we actually control what AI agents can do in our environment?”
This is the answer.
- Request a demo of Oasis AAM to see how intent-aware, just-in-time access works in your environment.
- Explore the Agentic Access Framework for the operating model behind AAM.
- Get certified with our NHI Management Fundamentals program to strengthen your foundations.
AI agents are already in the enterprise. Oasis Agentic Access Management ensures they stay safe, governed, and accountable.
We do newsletters, too
Discover tips, technical guides and best practices in our biweekly newsletter.